How GBSD Enables Advanced and Flexible Real-Time Fraud Blocking with its High-Trust, Mobile-Network-Embedded Softswitch
Think of the enormous value created by Google’s search engine or LinkedIn’s on-line directory. The knowledge networks these tech titans deliver are crucial to the economic livelihood of millions of businesses and professionals.
But there’s a risk inherent in these massive systems for they concentrate power in the small number of companies and people who “pull the levers” of the digital world.
Imagine if a few incompetent or dishonest persons gained control of key machine learning algorithms at Google or LinkedIn. They could cause enormous damage.
But whether we like this concentration of power or not, the tech world is moving relentlessly in this direction. Across the board, the cost-saving power of automation and machine learning is influencing businesses — of all sizes — to put greater trust in digital systems designed and managed by small teams of experts.
Last year I interviewed Larry Schwartz, the CEO of Seaborn, the company that built Seabras-1, the first independent undersea fiber cable connecting New York and Brazil. This was an enormous $500 million telecom project, and yet the Seaborn team fully designed and managed the project with only 25 people on staff. They secured investments, sold capacity, and managed contractors who manufactured the cable and laid it on the ocean floor across 10,800 kilometers.
So what’s the right risk management formula for managing mission-critical telecom projects? Well, consider the unusual method of the ancient Babylonians:

Risk management expert Nassim Taleb explains the Babylonians’ reasoning: “The builder knows how the building was made and could easily hide careless work in the building’s foundation that an inspector would never detect”. So we could say the builder has real “skin-in-the-game” — not coincidentally the title of Taleb’s latest book :- )
Fortunately, 3,800 years later, we’ve gotten much better at managing construction risks. When’s the last time you read a story about buildings or bridges collapsing? . . .unless, of course, an earthquake rumbled through.
In the tech world of today, managing risk is mostly about verifying the integrity, experience, and operating pedigree of the solution supplier and its key people.
Now one small company who’s built a solid reputation for delivering mission-critical mobile network systems is GBSD Technologies out of Dallas, Texas.
Competing against the huge network equipment firms, GBSD has carved out a niche enabling real-time MNO fraud management as it partners with prominent telecom fraud detection players. Details on GBSD’s business are covered in my recent interview with Jeffrey Ross, the firm’s Chief Operating Officer:
Dan Baker, Editor, Black Swan: Jeffrey, your company operates in a very interesting corner of the telecom fraud and security space. Can you explain that to us?
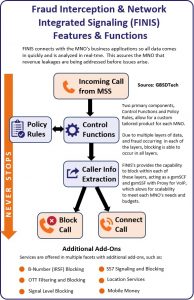
Jeffrey Ross: Be happy to, Dan. Since our startup in 2003, GBSD has been offering location-based services for mobile operators. And today our FINIS solution is in place at dozens of operators around the globe where we block fraudulent voice calls; filter out illegal SMS messages, prevent mobile money fraud, and assist with lawful intercept.
Location checks are increasingly in demand. For example, if you normally use your credit card in the US, and it suddenly appears in a European credit card transaction, that event will surely be flagged for possible fraud. Such monitoring is especially vital in mobile money systems because the cell phone is acting like a debit card.
On the fraud blocking side, FINIS is increasingly used to store blacklisted numbers to stop Wangiri, SIM box bypass, fraudulent SMS routing, and IRSF frauds in real-time.
Now, a point of clarification: aside from our location-based expertise, GBDS is not really in the fraud detection business. Can we detect, yes, but why reinvent the wheel when there are other great vendors to work with. We merely act as the universal blocking point for the fraud detected by industry detection firms such as Araxxe, SIGOS, Fraudbusters, and others.
The beauty of FINIS is that it’s a close-to-the-network trusted platform that blocks fraud at many different levels. It reads a variety of protocols, receives detection data, and blacklists numbers as instructed by external applications. And we sell our solution direct to the mobile operator.
I can see where flexibility is so vital to a central platform like that. Fraudsters are always looking for new entry points to manipulate the network.
Exactly. A fraudster’s mindset kind of reminds of what it’s like raising a toddler. Kids are very clever at getting what they want. And when parents take steps to hide the cookie jar from them, soon enough kids figure out where the cookie jar went.
I’m relatively new to the telecom industry, but the banking industry — where I come from — faces many of the same fraud patterns.
Currencies such as dollars, euros, and pesos were secure till fraudsters invented counterfeit currency. Cashier’s checks were a great substitute for cash till criminals invented counterfeit cashier’s checks. And not long ago, debit cards with magnetic strips were considered very safe, but now banks need to embed a sim chip on their cards.
So it never ends: you must constantly bring in newer and better fraud-fighting technology. And yet, you’ve got to be careful because fraudsters will often go back to the same old tricks they used successfully in the past.
Can you give us a quick backgrounder on the technical capabilities of FINIS?
Sure. FINIS is a softswitch that combines the roles of softswitch, gateway, SS7 firewall, and fraud blocker.
FINIS is also a high performance, real-time platform. To give you an idea: we screen messages at the rate of up to 40,000 SMSs per second, and that means tearing apart those SMSs, finding the numbers and turning them into A/B numbers to bounce off a blacklist for call blocking.
Now at the core of FINIS is a software kernel that’s rock-solid. That kernel never changes because it’s been used and tested in labs all over the world for years and years.
But we do perform lots of customization by vertically integrating to that trusted core through protocol stacks, network probing hardware, databases, Big Data analytics, you name it.
Customizing the upper layer of FINIS allows you to implement very specific security and fraud rules. For instance, fraudulent location requests across the emergency services network can be screened, and we can setup rules to block location requests that are not associated with a 112, 911 or 999 emergency call. And that’s very useful to prevent outsiders from peering inside the MNO’s network.
In mobile money, it’s useful to do a vicinity check when a subscriber wants to add money to their account and the agent is nearby. If the vicinity check finds the subscriber is in Mozambique and the agent is in Kenya, the transfer is blocked. So all sort of rules like that are built into FINIS. Another fraud rule we implement is to block an off-net and on-net SIM box calls.
Maintaining a mission critical fraud-blocking system at the heart of a mobile network is a big responsibility. How have you gained the trust of MNOs being a small organization?
Well, GBSD is small, but we are a highly experienced player, and regularly compete with network providers the likes of Ericsson and Huawei.
Clearly a mobile operator’s biggest concern is dropped calls. So you need to be agile enough to confront dropped call issues whatever hour of the day that occurs.
I can guarantee you, no matter where we go, the first thing they ask us is: what do you do, and how long have you been doing it? You have to have the stability and what it really comes down to, you have to fall back and say, “We have customers and have been doing this for years and years — and here’s our track record.” And you have to be able to prove that.
So it’s a matter of trust. An operator’s top network people have skin-in-the-game. They are responsible when there’s a network failure so they take that responsibility very seriously. There’s huge liability here. If our softswitch doesn’t put a call through, it’s not going to connect.
But ensuring five 9’s uptime is not simply a matter of what’s done on our end. It also matters how well you work with the mobile operator’s team. A year or two ago, one of our customers had a massive blackout — a huge power outage that affected the network. And equipment was dropping the load one after another, like dominos.
Fortunately, we work well with the guys in the switch room — and in the IT department. And together we soon had everything back up and running as if nothing ever happened.
Obviously, a lot of that emergency work cannot be done effectively from Dallas, Texas. So, a big part of the service we provide is to have system experts available on-location: we have FINIS guys scattered across Sub-Saharan Africa and Southeast Asia.
Jeffrey, it’s a great service you deliver. I’m impressed that you bridge the worlds of fraud control and highly available mobile networks by customizing the interface to the fraud detection players.
Dan, each opco or MNO is somewhat unique. Their subscriber sizes are quite different and so are their budgets.
But we explain to them how we can custom tailor FINIS to meet each operator’s needs. And our ability to get that job done with a small, dedicated team is a big advantage we have over our much larger competitors.
When we go in, we show everybody the Mercedes version of FINIS — which they all love to see. But often the operator doesn’t need all the bells and whistles and may ultimately chose the Volkswagen — or a model somewhere in-between.
Our goal is to provide peace of mind by getting them the fraud blocking platform they need, but also show them a roadmap to the broader capabilities they can ultimately have built into their FINIS platform.

