SIM Boxing Detection Challenges: When Legitimate Traffic Pays the Price
Your network operations center receives an alert at 3 AM: unusual call volume from Nigeria routing through a European interconnect. The CLI is properly formatted, call durations average 90 seconds, and the traffic profile matches a known enterprise customer’s campaign.
Do you block it and risk angering a paying client? Or let it through and potentially hemorrhage revenue?
This is the impossible choice carriers face in 2026. SIM boxing has evolved beyond crude bypass schemes. Modern operations use genuine local SIM cards, mirror legitimate traffic patterns, and exploit the same routing paths that real businesses depend on.
Traditional telecom fraud detection operates on pattern recognition, but when fraud perfectly mimics legitimacy, those tools become blunt instruments. At 1Route, we’ve built solutions recognizing that the detection challenge isn’t just technical—it’s a trust problem requiring validation at the source.
Key Takeaways for Busy Network Teams
SIM boxing detection is a trust problem, not just a technical challenge. Modern fraud mimics legitimate traffic so effectively that aggressive detection damages customer relationships and revenue. Effective telecom risk management requires:
- Multi-layered validation at network ingress, core signaling, and device endpoints
- Real-time decision making that distinguishes legitimate international business from fraudulent bypass schemes
- Cross-border authentication that works across both IP and legacy TDM infrastructure
- Systems that validate traffic at the source before fraudulent calls connect or legitimate calls get blocked
Why Is SIM Boxing So Hard to Detect?
SIM boxing is the practice of routing international calls through local SIM cards to avoid interconnect fees, making expensive cross-border traffic appear as cheap local calls. It’s telecom arbitrage dressed up as normal business.
If you’re a carrier operations manager or fraud analyst, you know the frustration: your SIM boxing fraud detection systems are sophisticated, your rules are tuned, and yet fraudsters slip through because they’ve mastered the art of looking boringly legitimate.

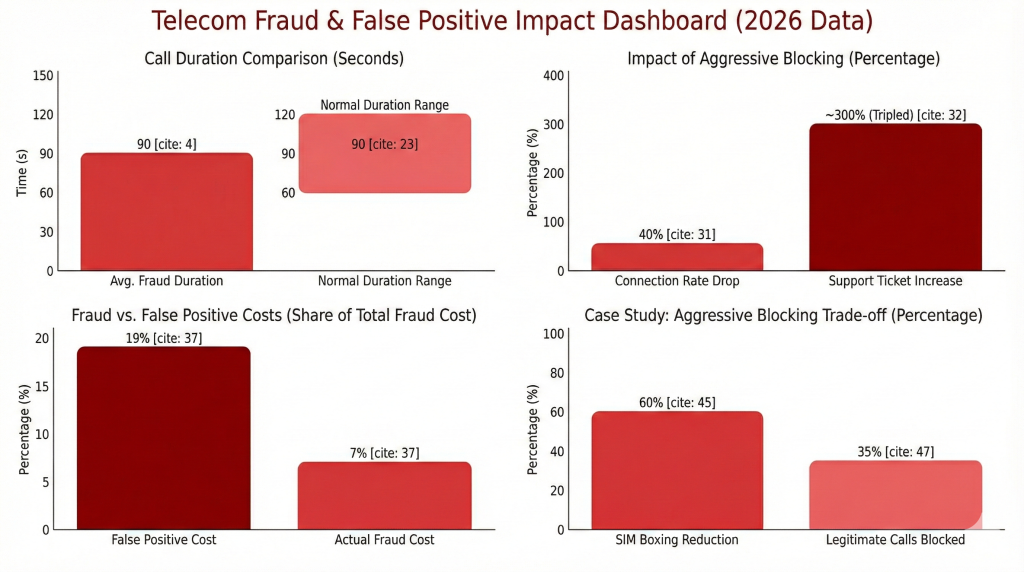
Here’s what makes SIM farm detection so challenging. Fraudsters don’t announce themselves with sudden traffic spikes. Instead, they mimic real subscriber behavior with theatrical precision. They use local CLIs that pass format validation. Call durations are kept between 60 and 120 seconds because that’s what normal conversations look like. Traffic is spread across multiple SIMs to avoid volume thresholds. Business hours are even carefully observed.
The result? Fraud that behaves so suspiciously normal it bypasses caller trust mechanisms entirely. Your legitimate traffic identification tools can’t distinguish between a SIM box routing 500 calls per day and a small call center doing the same thing.
Aggressive blocking crushes real business while sophisticated operations simply adjust their patterns and continue.
The Hidden Cost of Getting It Wrong: False Positives and Lost Trust
When detection leans too aggressive, the damage ripples outward in ways that monthly fraud reports never capture.
Consider a European carrier that tightened SIM boxing controls after a major revenue loss. Within two weeks, enterprise customers began reporting blocked conference calls. International contact centers saw connection rates drop 40%. Support tickets tripled. The NOC was drowning in escalations from partners whose traffic looked “suspicious” simply because it crossed three countries.
False positives in fraud detection aren’t just a tuning issue. They’re a trust erosion problem. Blocking a legitimate call tells a business partner you don’t trust their traffic. Flagging an international route tells an enterprise client their business doesn’t matter. An overly sensitive rule tells the market you’ve chosen protection over partnership.
JPMorgan Insights research on card-not-present fraud reveals that false positive losses can actually outweigh actual fraud itself, with false positives representing 19% of total fraud costs compared to just 7% from actual fraud. Telecom faces a similar dynamic.
The FCC STIR/SHAKEN Robocall Mitigation Requirements aim to reduce unwanted calls, but they don’t address the fundamental challenge: How do you stop fraud without stopping business? How do you validate traffic without breaking trust?
Case Study: When SIM Boxing Slipped Through—and Legitimate Calls Paid the Price
[This is a composite example based on patterns 1Route observes working with carriers in high-fraud markets globally.]
A Tier 2 carrier in West Africa faced escalating SIM boxing losses that violated interconnect settlement rules. Their fraud team responded by implementing aggressive volume thresholds and CLI pattern matching across international routes.
The result? SIM boxing dropped 60%. Success, right?
Not quite. Legitimate enterprise traffic collapsed alongside the fraud. A regional airline’s reservation system started failing. An international bank’s call center saw 35% of calls blocked. Roaming traffic fraud flags caught actual roaming subscribers.
The key insight: stopping fraud without simultaneously validating legitimacy creates collateral damage that can exceed the original fraud losses. Detection without discrimination isn’t protection—it’s just different revenue loss.
What Traditional Detection Models Get Wrong About Legitimate Traffic
Here’s a not-so-fun fact: most telecom fraud analytics platforms were built to catch yesterday’s fraud patterns, not tomorrow’s. Traffic baselining models work beautifully when fraudsters cooperate by following predictable scripts. Unfortunately, they rarely do.
The real problem? Traditional detection operates in isolation. When a call bounces through three carriers before landing on your network, you’re seeing only one leg of the journey. Multi-carrier routing creates blind spots where SIM boxing operators hide in plain sight.
Picture this: a fraudster routes 10,000 calls through legitimate operator A, who passes clean traffic to operator B, who finally delivers it to your network. You see perfectly normal volume from a trusted source. Operator A sees nothing unusual either. The fraud is invisible because no single carrier holds the complete picture.
This explains why rule-based fraud detection struggles with evolving tactics and fixed thresholds, as demonstrated in a recent Eusipco research on hybrid machine learning approaches. When fraud shifts faster than your rules update, you’re left chasing ghosts or blocking real customers.
Add latency and QoS trade-offs into the mix, and post-call analysis becomes a game of “spot the fraud after the damage is done.” Can you really bring trust back to voice when you’re always one step behind?

5 Practical Ways to Reduce SIM Boxing False Positives
- Validate traffic at network ingress, not after connection
Stop fraud at the door. Real-time signaling inspection during call setup lets you reject suspicious traffic before it consumes network resources or reaches subscribers. Post-call analysis is useful for forensics, but prevention beats detection.
- Combine signaling intelligence with call authentication
SS7 and SIP signaling reveal patterns invisible to call detail records alone. Cross-referencing STIR/SHAKEN attestation levels with signaling behavior catches inconsistencies that single-layer analysis misses.
- Treat international traffic as a trust challenge, not a threat
Deploy network visibility tools that distinguish between established business routes and suspicious new patterns. Legitimate enterprises don’t suddenly route 5,000 calls through a previously dormant interconnect at 3 AM on Sunday.
- Support both IP and legacy TDM environments
SIM boxing operators exploit gaps between modern and legacy infrastructure. If your fraud prevention only works on all-IP networks, you’re leaving half your perimeter undefended.
- Prioritize real-time decisions over retrospective analysis
Deploy systems that make block/allow decisions in milliseconds. The difference between real-time and delayed response is the difference between prevention and damage control.
How 1Route Tackles SIM Boxing Detection Challenges at the Source
1Route’s approach starts with a simple principle: stop fraud before the phone rings.
Our three-pillar defense operates simultaneously across network ingress, core signaling, and device endpoints:
- EDGE Computing Solution validates inbound traffic at network entry, verifying STIR/SHAKEN attestation and blocking fraudulent calls during setup.
- The FINIS Platform acts as a firewall within SS7, Diameter, and SIP signaling infrastructure, intercepting SIM boxing attempts in real time.
- Finally, On-SIM protection secures subscriber identity at the device level.
We validate, block, and protect across multiple layers before fraudulent traffic reaches your subscribers or strains your fraud operations centers. Legitimate international calls flow freely while SIM boxing schemes hit a coordinated defense at every intervention point.

1Route and the Future of Trusted International Voice Traffic
Cross-border voice operates where inter-operator data sharing limits and misaligned carrier trust frameworks leave legitimate calls vulnerable. STIR/SHAKEN, widely adopted in the United States to authenticate caller identity, was not originally designed for international traffic and international calls remain largely outside its protective reach.
1Route addresses this gap by serving as an international clearing house that validates calls crossing borders. Our EDGE Computing Solution enables non-US carriers to achieve accurate A-level attestation for traffic entering the United States.
The GLF’s annual Fraud Report 2025 highlights that 77% of carriers plan to increase investment in fraud detection for voice and messaging. The future of trusted international voice depends on systems that validate traffic at the source and treat cross-border routing as a trust-building opportunity.
FAQ: Rethinking SIM Boxing Detection Challenges
SIM boxing isn’t just hard to detect because fraudsters are clever. It’s hard because trust has been stripped from the phone itself.
Why does SIM boxing resemble legitimate traffic so closely?
SIM boxing operators use local SIM cards with valid CLIs, realistic call durations, and expected traffic volumes.
Why are international calls more likely to be misclassified?
Multi-carrier routing creates visibility gaps. Traditional systems see only one leg of the journey, missing fraud hidden in previous hops.
Is STIR/SHAKEN alone enough to stop SIM boxing?
No. While the STIR/SHAKEN framework validates caller identity, it doesn’t address TDM networks or cross-border attestation gaps. FCC enforcement actions increasingly recognize this limitation.
How can carriers reduce false positives without increasing fraud risk?
Deploy multi-layered validation that respects E.164 numbering standards and validates traffic at network ingress before connection.
The real challenge is restoring confidence without blocking real business. This requires systems that treat international traffic as a trust opportunity rather than a threat.

